State Examination Support
Virginia State Examination Preparation
Understanding where your policies and procedures meet the VA SCC examination for brokers and lenders. Updates to cybersecurity regulations add specificity to Virginia's request
Last updated on 03 Nov, 2025
We have compiled this guide to align with the order in which questions appear in the questionnaire, not with their significance or depth of response. Some questions are very specific, and others are overwhelmingly general "catch-all" questions.
Vendor Management - 3rd Party Processors

This question requires pulling your 7-50 Vendor Management policy if you use 3rd party processing.
Hot Button - "Pre-Approved"
Virginia has rules regarding the term"pre-approved" and requires that you only use it with an actual offer of credit. This means you must review your pre-qualification policy (2-40 Fair Lending)

Hot Button - Advertising
The examiner reviews all advertising, social media, and websites and checks independently to see if you have omitted anything. Furthermore, there are honeypots where examiners often receive copies of advertising directed at consumers, so also exercise a robust review before submitting. You should use your 2-34 Advertising Policies and Procedures checklist to ensure compliance.

The "Catch-All"... All Policies and Procedures
This provides the reference for all of your compliance-related answers. The Compliance Pack 1-Quality Control, 2-0 Compliance and 2-9 IT Security Plan - also known as the Compliance Pack for your business model which you purchased here: https://www.mortgagemanuals.com/broker-non-del-compliance-pack.html

Detailed Supplemental Questions
You can best answer these by referencing your policies. This avoids potentially providing narrative descriptions/answers that contradict policy or compliance.

IT Security Supplement
in 2022, the FTC undertook a massive update to CyberSecurity requirements for companies handling consumer information. Of course, mortgage companies hold a treasure trove if this information, so the examination prioritizes reviews of these areas.
Fortunately, Virginia examiners do not reinvent the wheel and follow the FTC protocols exactly, so you can address these items by pointing out where, within your policies, the examiner can locate the items by using our matrix.
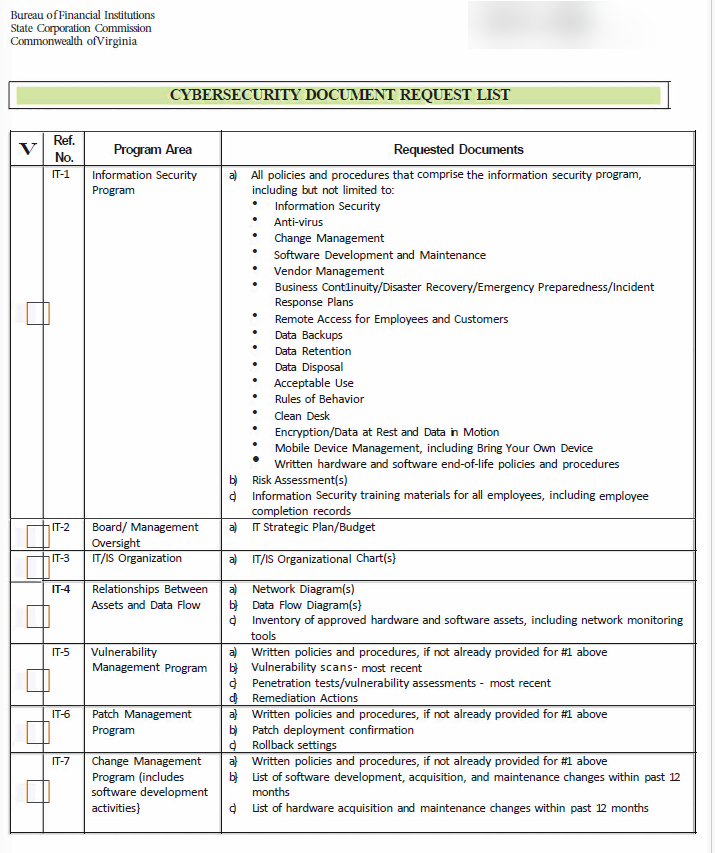
Where to locate items - Provide this spreadsheet
Please note that some requirements are not policy/procedure related, so you must create a list of your hardware, network devices and organization, users, etc.
