Compliance
When a Customer Falls for a Hacked Email: What to Do Next
It’s every lender’s nightmare: a borrower receives a hacked email that looks legitimate, wires funds to the fraudster’s account, and suddenly the closing is in jeopardy. Unfortunately, this type of wire fraud has become one of the fastest-growing cybercrimes targeting mortgage transactions. Under your 2-9 IT Security Program, you should be prepared with a structured response plan to minimize loss, assist the customer, and demonstrate compliance to regulators.
Last updated on 07 Nov, 2025
Step 1: Immediate Containment
Notify the Bank – The first and most urgent step is to instruct the customer to contact their sending bank’s fraud department immediately. Banks can sometimes initiate a SWIFT recall or freeze funds if the transfer is reported quickly.
Engage Receiving Institution – Work with law enforcement and the receiving bank (if known) to flag the account and prevent further disbursement.
Step 2: Incident Reporting and Escalation
Internal Notification – Alert the firm’s Information Security Officer and senior management in line with your 2-9 escalation policy.
Regulatory Reporting – If sensitive customer information was compromised, evaluate whether notification under the Gramm-Leach-Bliley Act (GLBA) or state data breach laws is required.
File SAR if Applicable – Under BSA/AML obligations (referenced in the Quality Control Plan, Section 1-70), if the transaction appears to involve fraud or criminal intent, the designated BSA Officer should consider filing a Suspicious Activity Report (SAR).
Step 3: Customer Assistance
Guidance and Support – Provide the borrower with written instructions, including the exact steps to take with their bank and law enforcement (FBI’s IC3.gov reporting portal).
Clarify Liability – While funds are often unrecoverable, maintaining transparency helps protect the lender’s reputation and shows regulators that proper consumer-protection protocols are followed.
Step 4: Forensic Review
Email Security Audit – Determine how the fraudulent communication reached the customer: was it a compromise of the title company’s account, a spoofed domain, or a hacked borrower inbox?
System Safeguards – Review whether the firm’s own IT systems were breached. Section 2-90-21 of the IT Security Policy (Email Security & Phishing Prevention) should be referenced to confirm technical safeguards such as SPF, DKIM, DMARC, and employee phishing training.
Step 5: Preventive Measures Going Forward
Wire Transfer Policy – Reinforce the “call-back” procedure outlined in 2-90-36, requiring verbal confirmation of wire instructions using a verified phone number.
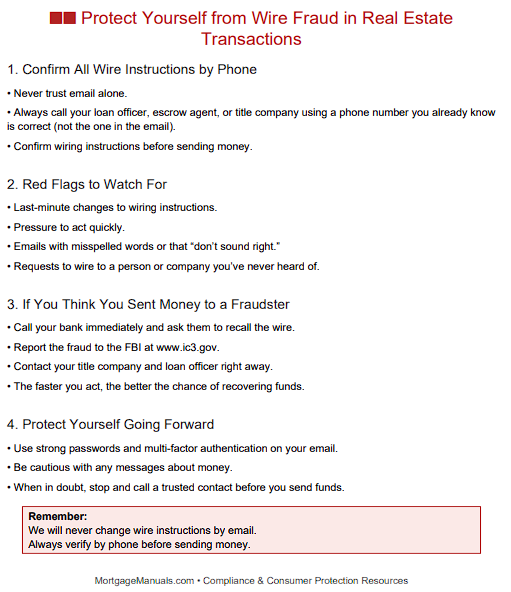
Customer Education – Provide borrowers with a one-page “Wire Fraud Warning” at application and again prior to closing, advising them never to trust last-minute emailed wiring instructions.
Vendor Oversight – Confirm that settlement service providers (title/escrow companies) maintain their own Written Information Security Programs (WISPs) aligned with GLBA Safeguards.
Conclusion
When customers fall prey to a hacked email, the funds may or may not be recovered—but your response as a mortgage company is critical. By following the structured approach in the 2-9 IT Security plan—containment, reporting, customer support, forensic review, and prevention—you demonstrate due diligence, protect your reputation, and most importantly, maintain compliance.
