Georgia Ad-Hoc Requests for BSA/AML and IT (Safeguarding) Security Plans
State Examination Support
Georgia Ad-Hoc Requests for BSA/AML and IT (Safeguarding) Security Plans
We have received numerous requests from companies who are NOT under a current examination or have recently completed an exam to provide specific plans. Here are instructions for how to locate, extract, and give these SPECIFIC plans to the regulator.
Last updated on 10 Nov, 2025
Georgia has expanded its request to include greater specificity, likely because respondents weren't clear enough. For customers who have purchased a "Compliance Pack," responding to this is as simple as following the instructions below.
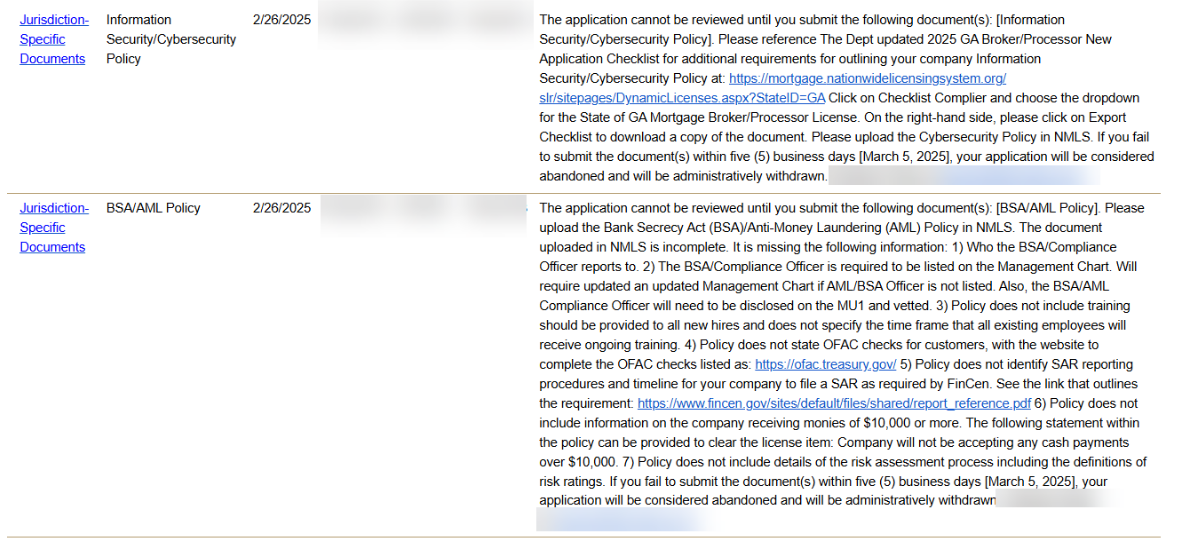
Common Deficiencies and their location
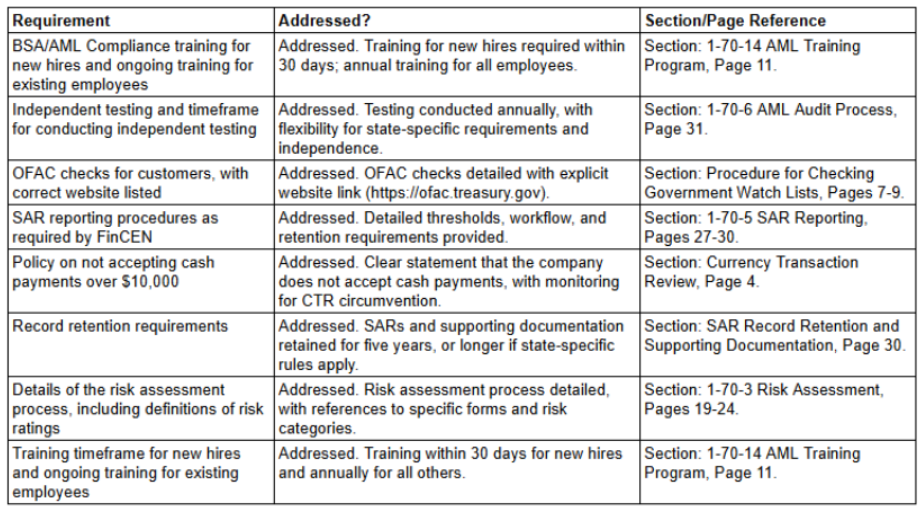
Sample Form Letter from GA
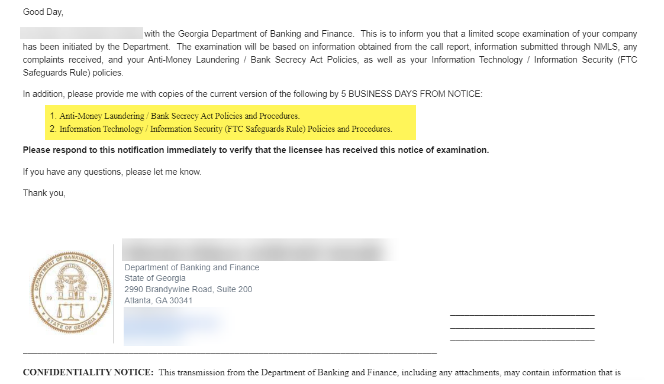
Step-by-Step Response Guide
This guide provides a detailed process for extracting the 1-70 AML Plan from the 1-0 or 1-A Quality Control (QC) Plan, and the 2-90, 2-91, and 2-92 IT Safeguarding Policies and Procedures from the 2-9 IT Security Plan. If you have purchased these as stand-alone policies, you can ignore locating them on your pages. Follow these steps to accurately isolate and document the relevant sections for individual use.
Extracting the 1-70 AML Plan from the 1-0 or 1-A QC Plan
Access the QC Plan Document:
pen the 1-0 or 1-A Quality Control (QC) Plan document. Ensure that you are working with the most current version.
Locate Section 1-70: Scroll through the table of contents to find Section 1-70 (AML Plan). Alternatively, use the document's search feature (e.g., press Ctrl + F on a keyboard) and search for "1-70" or "AML Pian."
Review Section 1-70 Content:
Ensure you are looking at the ENTIRE AML Plan, from 1-70 all the way to 1-70-6 (the entire section, not just the first few pages):
Access the IT Security Plan Document: Open the 2-9 IT Security Plan document. Confirm that the version you are working on is the latest.
Locate Sections 2-90, 2-91, and 2-92: Use the table of contents or the document search feature to find the following sections: Section 2-90: IT Safeguards Overview Section 2-91: Physical and Logical Access Controls Section 2-92: Incident Response Procedures
Review the Content of Each Section: Verify that each section contains the necessary information: 2-90: General overview of IT safeguarding policies. 2-91: Detailed physical and logical access control measures. 2-92: Steps and protocols for incident response, including breach notification procedures.
Print page range to *.PDF: Note the pages to print (custom range approximately 50 pages) Save each document with appropriate filenames to match the regulator request such as, e.g.: "Information Technology / Information Security (FTC Safeguards Rule) Policies and Procedures." Attach this file to your email response and store the file in your policy and procedures folders for future reference.
Updated 3/6/2025 - Georgia is also holding new applications for this material